Iptables And K8S
Iptables
CentOS: Iptables 说 Netfilter 是工作在内核的模块,Iptables 是工作在用户空间、负责定义规则的命令行工具:
Iptables is the userspace module, the bit that you, the user, interact with at the command line to enter firewall rules into predefined tables. Netfilter is a kernel module, built into the kernel, that actually does the filtering.
基本概念
Tables
There are currently five independent tables (which tables are present at any time depends on the kernel configuration options and which modules are present).
- filter
- nat: This table is consulted when a packet that creates a new connection is encountered.
- mangle: This table is used for specialized packet alteration. Until kernel 2.4.17 it had two built-in chains: PREROUTING (for altering incoming packets before routing) and OUTPUT (for altering locally-generated packets before routing). Since kernel 2.4.18, three other built-in chains are also supported: INPUT (for packets coming into the box itself), FORWARD (for altering packets being routed through the box), and POSTROUTING (for altering packets as they are about to go out).
- raw: This table is used mainly for configuring exemptions from connection tracking in combination with the NOTRACK target.
- security
Chains
Tables consist of chains, which are lists of rules which are followed in order.
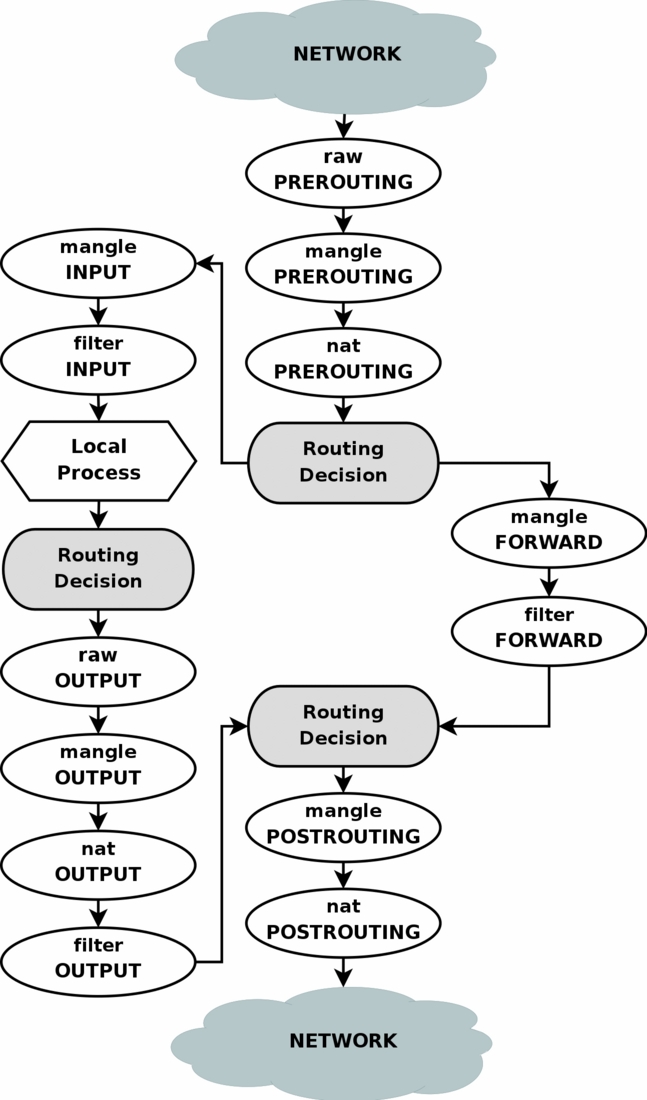
Traversing Chains
A network packet received on any interface traverses the traffic control chains of tables in the order shown in the flow chart. The 3 most commonly used targets are ACCEPT, DROP, and jump to a user-defined chain.
安装
安装 iptables :
1 | |
打开 iptable_nat 内核模块:
1 | |
使用
K8S
Kubernetes: iptables proxy mode 提到 kube-proxy 在 iptables proxy 模式下会利用 iptable 工作:
For each Service, it installs iptables rules, which capture traffic to the Service's clusterIP and port, and redirect that traffic to one of the Service's backend sets. For each Endpoint object, it installs iptables rules which select a backend Pod.
本文会探索 Kubernetes 如何利用 iptables 以达到路由流量的目的。
1 | |